You can use authorizations to protect your data from unauthorized access. Authorizations restrict access to data in order to avoid business risks and financial losses due to error, mistakes or negligence.
Furthermore, it is also a matter of treating personal data confidentially. Think for example of personal data from HR processes or customer data. This information can cause a lot of damage if it falls into the wrong hands.
NextTables protects your data on several levels. On the one hand, the access on the table level is controlled by its own authorization object. This allows you to define which users can display or change data in a table. Using so-called apps, you can bundle a number of tables into one application and thus control access to a group of tables in a targeted manner. For each user, you can define who can only read table contents and who can change the table contents.
In addition, you can specify that certain users cannot see an application at all. See the following figure for an illustration.
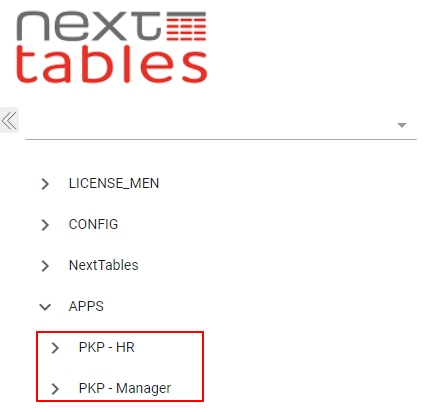
It represents the process of personnel cost planning, which is divided into two apps: HR and Manager. Via permissions you can control that the HR department only sees the tables under the PKP-HR-app and the line managers only see the tables of the PKP-Manager-app.
You can also appoint administrators who are allowed to create the configuration or customize the application.
In addition, standard SAP authorizations also apply when accessing InfoProviders. These authorizations are required by all users, for example to call up reports or maintain new entries. This authorization check deals with general access to InfoProviders. There is no access restriction to the data contents of the InfoProviders.
Access to the information itself is restricted by so-called analysis authorizations. These restrict access to the data content of the InfoProvider. This allows you to release certain content for a user and to assign very granular authorizations. For example, one user may only see the data of one company code and another user may see the data of another company code. However, the information for both company codes is located in the same InfoProvider.
Learn all about easy Data Maintenance with NextTables
When analysis authorizations are used, NextTables automatically generates variables for each InfoObject that is marked as authorization-relevant. You can select the variables in the global filter.
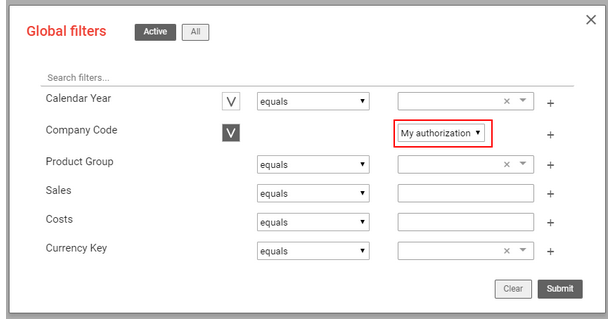
Thus, the user only sees the data for which he is authorized.
Why do we use variables? Well, when variables are used, the user understands that his view is restricted and may therefore look different from the view other users see. Also, templates/bookmarks with variables can be created and shared so that each user can see "his" data.
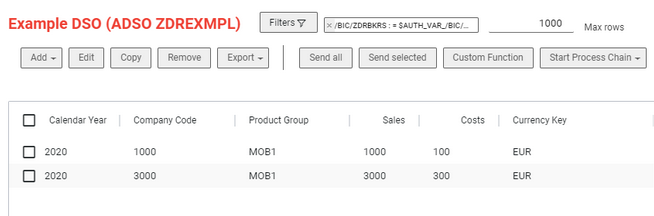
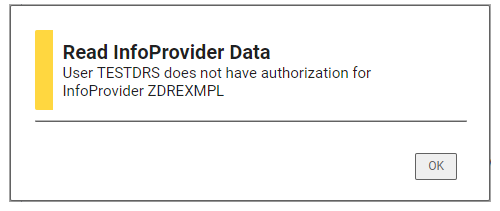
If the user tries to access data outside of his authorization, he receives an error message.
An authorization check is also carried out when the data is written back. All values that are updated by the user must be within their authorizations.
NextTables supports authorizations for both DSOs and InfoObjects. Compound InfoObjects are also supported.
Summary
As you can see, NextTables protects your data from unauthorized access in various ways. The use of variables ensures that user-friendliness is not compromised. If you are interested in the technical implementation of permissions, this article from our NextTables knowledge base will help you.
Do you want to learn more about NextTables? Download our presentation on NextTables now and find out everything about other application scenarios and functions!
Would you like to learn more about NextTables? Download our presentation on NextTables now and learn all about further usage scenarios and functions.
NextTables, NextTables Use Cases

/Logo%202023%20final%20dunkelgrau.png?width=221&height=97&name=Logo%202023%20final%20dunkelgrau.png)